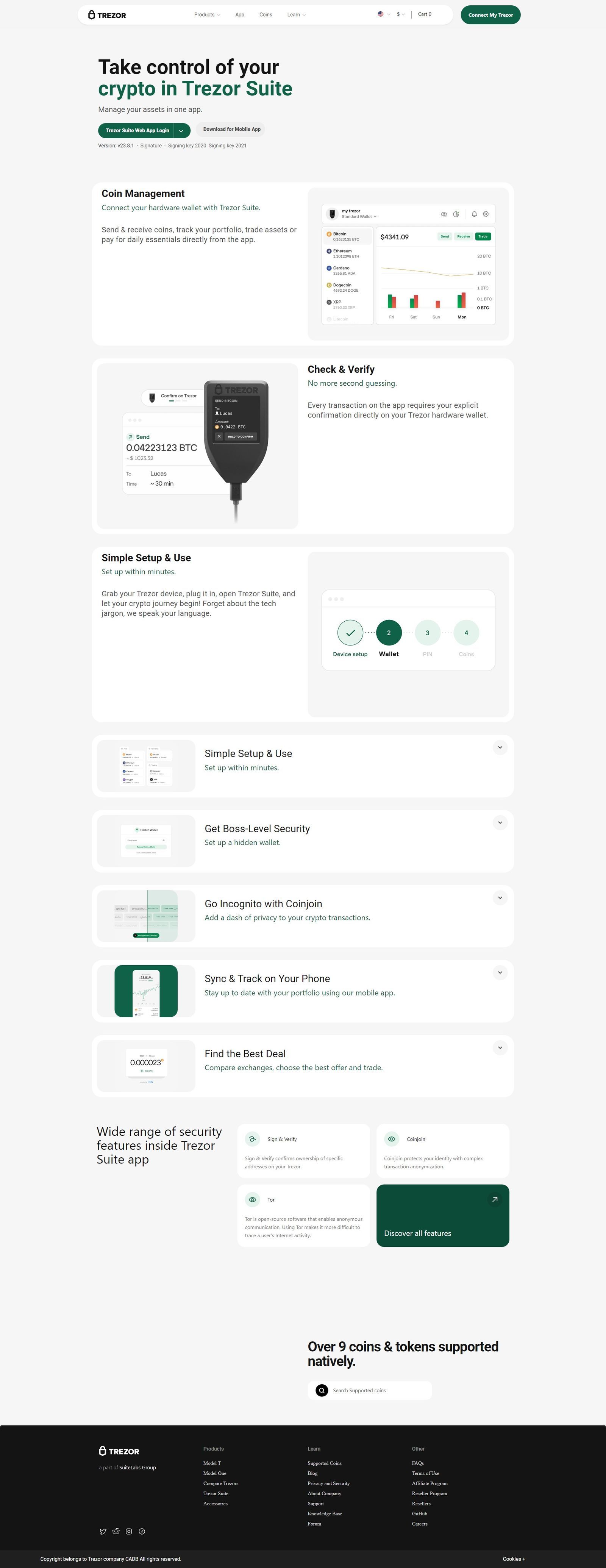
Trezor Login: A Secure Gateway to Your Crypto Assets
As cryptocurrency adoption accelerates worldwide, security remains a primary concern for investors. Trezor, a trusted name in the crypto space, offers an unparalleled level of protection through its hardware wallets. However, understanding how to perform a Trezor login securely is crucial for maximizing your digital asset safety. This article explores the Trezor login process, its security features, and best practices for secure usage.
What is Trezor?
Trezor is a hardware wallet developed by SatoshiLabs, designed to store private keys offline. Unlike software wallets or exchange-based accounts, Trezor provides a secure physical environment that protects your crypto from hacking, phishing, and malware threats. It supports a wide range of cryptocurrencies, including Bitcoin, Ethereum, Litecoin, and ERC-20 tokens.
Trezor Login: Not Your Traditional Login
Trezor does not use a typical username and password login system. Instead, it authenticates access via a physical device connection and PIN verification. This means you cannot log into your Trezor wallet without having the device physically present.
Here’s a step-by-step guide on how to perform a Trezor login:
1. Connect Your Trezor Device
Start by connecting your Trezor Model One or Trezor Model T to your computer or mobile device using a USB cable. If it’s your first time, ensure you’ve initialized the device and stored your recovery seed securely.
2. Visit Trezor Suite
Go to the official Trezor Suite platform by typing suite.trezor.io into your browser. Trezor Suite is the recommended software interface that provides a secure environment for managing your assets.
3. Authenticate with PIN
Once the device is detected, you’ll be prompted to enter your PIN. This PIN acts as a local security layer and prevents unauthorized access in case your device is lost or stolen. Enter the digits as displayed on your Trezor device using the blind matrix system to avoid screen-based keyloggers.
4. Access Your Dashboard
After entering the correct PIN, you’ll gain access to your wallet dashboard. From here, you can send, receive, manage assets, and review transaction histories—all without exposing your private keys to the internet.
Security Features During Trezor Login
Trezor incorporates multiple security layers that protect users during the login process:
- Two-Factor Authentication (2FA): While Trezor itself doesn’t require external 2FA, the device acts as a second factor, making phishing virtually impossible.
- Passphrase Encryption: An optional layer that adds a custom passphrase, known only to the user.
- Firmware Verification: Each time the device connects, it verifies the authenticity of installed firmware.
Best Practices for Safe Login
- Always Use Official Interfaces: Only access your wallet via the official Trezor Suite. Avoid third-party sites or extensions.
- Keep Firmware Updated: Regular updates from Trezor enhance security and add new features.
- Secure Your Recovery Seed: Never share or store it digitally. This is your ultimate backup.
- Avoid Public Wi-Fi: While Trezor is resistant to remote attacks, it’s wise to use secure connections.
Final Thoughts
The Trezor login process is designed with security and user-friendliness in mind. While it might differ from traditional logins, the physical authentication process drastically reduces the risk of cyberattacks. By following best practices and leveraging Trezor’s robust security features, users can confidently manage their cryptocurrency portfolios with peace of mind.
Made in Typedream